VeraCrypt App Introduction
VeraCrypt is a powerful, open-source disk encryption software designed to protect your sensitive data from unauthorized access. It builds upon the legacy of TrueCrypt, addressing security vulnerabilities and enhancing its features for modern computing environments. This comprehensive guide explores VeraCrypt's functionalities, security features, and how to effectively utilize it to safeguard your files and partitions on your Windows system.
Understanding VeraCrypt's Core Functionality
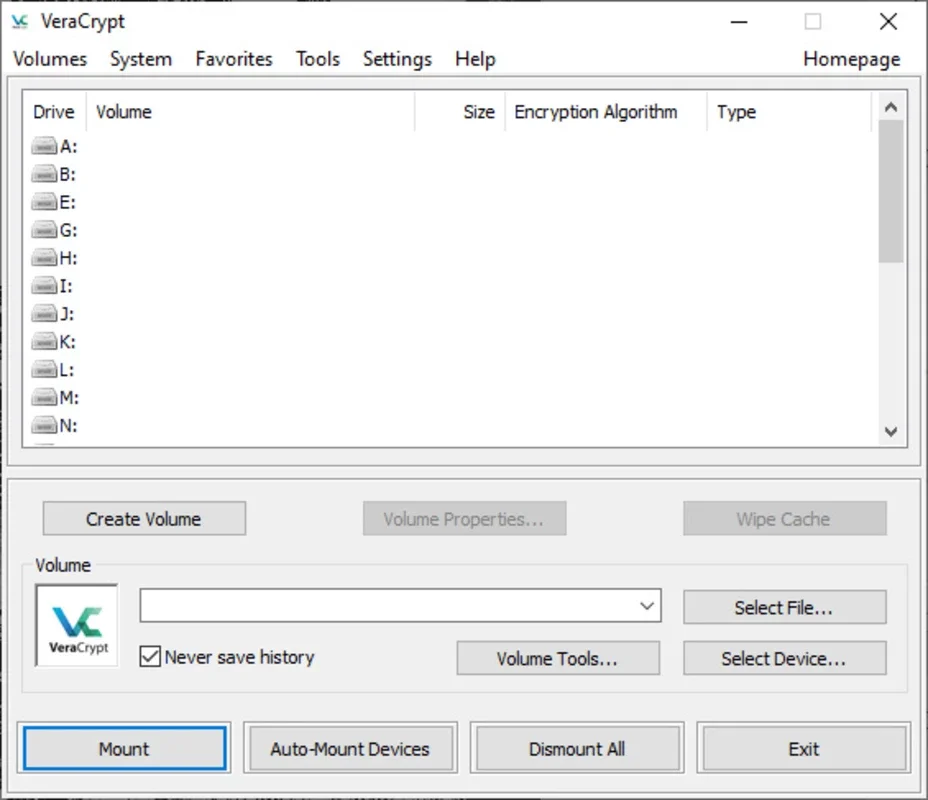
At its heart, VeraCrypt operates by creating encrypted containers, often referred to as virtual disks or volumes. These containers can reside within files or on entire partitions. When you mount a VeraCrypt volume, it appears as a regular drive letter in Windows Explorer, allowing you to interact with its contents as you would with any other drive. However, the data within is securely encrypted, inaccessible without the correct password or keyfile.
VeraCrypt employs strong encryption algorithms, including AES, Serpent, and Twofish, often used in combination for enhanced security. This layered approach makes it exceptionally difficult for unauthorized individuals to decrypt your data, even with sophisticated tools.
Key Features and Benefits
- Robust Encryption: VeraCrypt utilizes a combination of advanced encryption algorithms, providing a high level of security against brute-force attacks and sophisticated decryption attempts. The use of multiple algorithms provides redundancy and resilience against potential weaknesses in individual algorithms.
- Virtual Disk Encryption: Create encrypted containers (virtual disks) that can be stored anywhere on your system or removable media. This allows you to encrypt specific files or folders without encrypting your entire drive.
- Whole Disk Encryption: Encrypt entire partitions or drives, providing comprehensive protection for all data stored on them. This is ideal for securing your operating system and all its associated files.
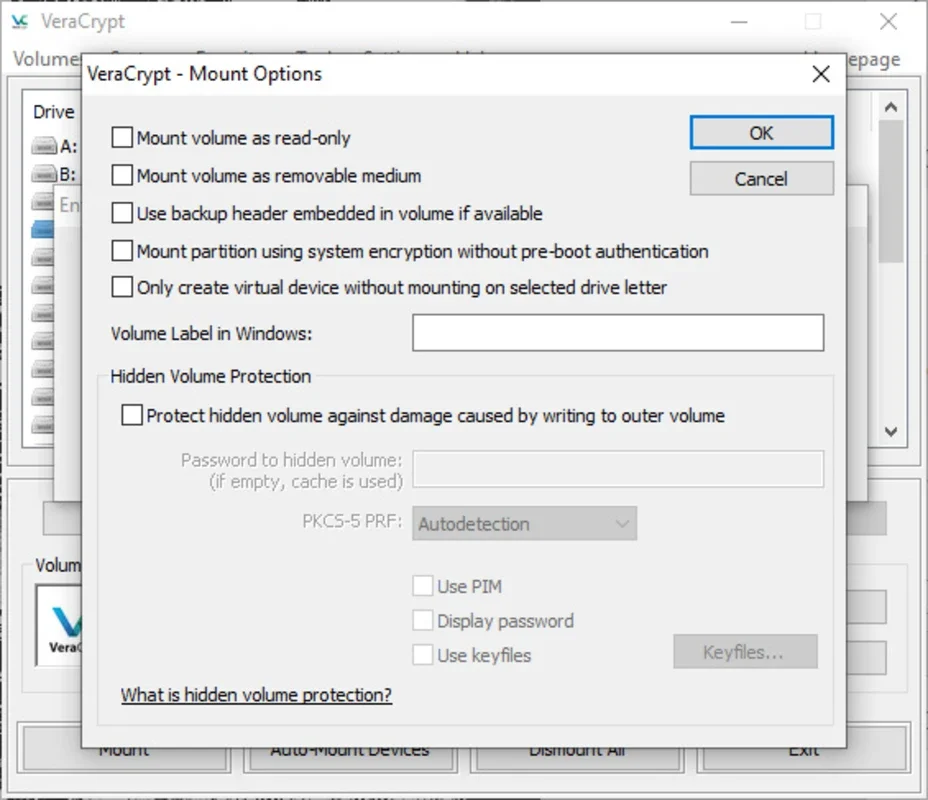
- Hidden Volumes: A unique feature allowing you to create a hidden volume within a larger, seemingly normal volume. This provides an extra layer of security, protecting your most sensitive data even if someone forces you to reveal the password to the outer volume.
- Open Source and Audited: VeraCrypt's open-source nature allows independent security researchers to scrutinize its code, identifying and addressing potential vulnerabilities. This transparency builds trust and confidence in its security.
- Cross-Platform Compatibility: While this guide focuses on the Windows version, VeraCrypt is available for other operating systems, including macOS and Linux, providing consistent security across different platforms.
- Ease of Use (Relative to its Power): While VeraCrypt's functionality is advanced, its interface is relatively intuitive, making it accessible to users with varying levels of technical expertise. However, careful attention to the setup process is crucial to ensure optimal security.
Setting Up VeraCrypt on Windows
- Download and Installation: Download the latest version of VeraCrypt for Windows from the official website. Ensure you download from a trusted source to avoid malware.
- Creating a Volume: VeraCrypt offers several options for creating encrypted volumes. You can create a file-based volume (encrypted container), encrypt a partition, or encrypt an entire drive. Choose the option that best suits your needs and security requirements. The process involves selecting an encryption algorithm, setting a strong password, and choosing a volume size.
- Mounting a Volume: Once a volume is created, you can mount it to assign it a drive letter. This makes the encrypted volume accessible in Windows Explorer.
- Using the Encrypted Volume: Once mounted, you can use the encrypted volume like any other drive, storing and accessing your files.
- Unmounting a Volume: When finished, always unmount the volume before removing any storage media or shutting down your computer. Failure to do so can lead to data corruption.
Security Best Practices
- Strong Passwords: Use long, complex passwords that combine uppercase and lowercase letters, numbers, and symbols. Avoid using easily guessable passwords.
- Keyfiles: Enhance password security by using keyfiles in addition to or instead of a password. A keyfile is a file that, when selected, is required to unlock the encrypted volume.
- Regular Updates: Keep VeraCrypt updated to benefit from the latest security patches and bug fixes.
- System Integrity: Maintain the overall security of your Windows system by regularly updating your operating system, antivirus software, and firewall.
- Caution with Removable Media: Be cautious when using removable media (USB drives, external hard drives) with VeraCrypt volumes. Ensure you unmount the volume before removing the media to prevent data loss or corruption.
VeraCrypt vs. Other Encryption Solutions
VeraCrypt stands out from other encryption solutions due to its open-source nature, robust encryption algorithms, and advanced features like hidden volumes. Compared to BitLocker (a built-in Windows encryption tool), VeraCrypt offers more flexibility and granular control over encryption settings. While BitLocker provides whole-disk encryption, VeraCrypt allows for both whole-disk and file-based encryption, offering greater versatility. Other commercial encryption solutions may offer user-friendlier interfaces, but VeraCrypt's open-source nature and advanced features make it a compelling choice for users prioritizing security and transparency.
Conclusion
VeraCrypt is a powerful and versatile tool for securing your data on Windows. By understanding its features and following best practices, you can significantly enhance the security of your sensitive information. Remember that strong passwords and regular updates are crucial for maintaining the effectiveness of VeraCrypt's protection. While it requires a bit more technical understanding than some simpler solutions, the enhanced security it provides is well worth the effort for those who need robust data protection.