Tails App Introduction
Tails is a live operating system, based on Debian, designed to protect your privacy and anonymity online. Unlike traditional operating systems, Tails runs entirely from a USB drive or DVD, leaving no trace on the host computer. This makes it ideal for accessing sensitive information or browsing the internet privately, ensuring your online activities remain confidential.
Key Features of Tails
- Built-in Tor Network: Tails routes all internet traffic through the Tor network, obscuring your IP address and making it extremely difficult to track your online activity. This is crucial for protecting your identity and location.
- Secure Default Settings: Tails comes pre-configured with security settings optimized for privacy. No user configuration is needed to achieve a high level of anonymity. This eliminates the risk of accidental misconfigurations that could compromise your security.
- No Persistent Storage: All data is stored in RAM and deleted when the system shuts down. This ensures that no information is left behind on the host computer, even if it's compromised.
- Regular Updates: Tails receives regular security updates to address vulnerabilities and maintain its high level of security. Staying up-to-date is essential for optimal protection.
- Open-Source and Verifiable: The Tails source code is publicly available, allowing independent security audits and verification of its integrity. This transparency builds trust and ensures accountability.
- User-Friendly Interface: While powerful, Tails uses the familiar GNOME desktop environment, making it relatively easy to navigate and use, even for users unfamiliar with Linux.
How Tails Protects Your Privacy
Tails employs several techniques to safeguard your privacy:
- Tor Network: As mentioned, Tor is the cornerstone of Tails' privacy features. It anonymizes your internet traffic by routing it through multiple relays, making it nearly impossible to trace your online activities back to you.
- HTTPS Everywhere: Tails automatically encrypts your connections to websites that support HTTPS, protecting your data from eavesdropping.
- No Persistent Data: This prevents any sensitive information from being stored on the host computer, even if it's compromised or accessed without your knowledge.
- Strong Encryption: Tails uses strong encryption to protect your files and communications.
- Regular Security Audits: The open-source nature of Tails allows for regular security audits, ensuring that any vulnerabilities are quickly identified and addressed.
Using Tails: A Step-by-Step Guide
- Download Tails: Download the Tails ISO image from the official Tails website. Verify the integrity of the downloaded file using the checksum provided.
- Create a Bootable USB Drive: Use a tool like Etcher to create a bootable USB drive from the Tails ISO image. Ensure you use a USB drive with sufficient storage capacity.
- Boot from USB: Restart your computer and boot from the USB drive. The boot process may vary depending on your computer's BIOS settings.
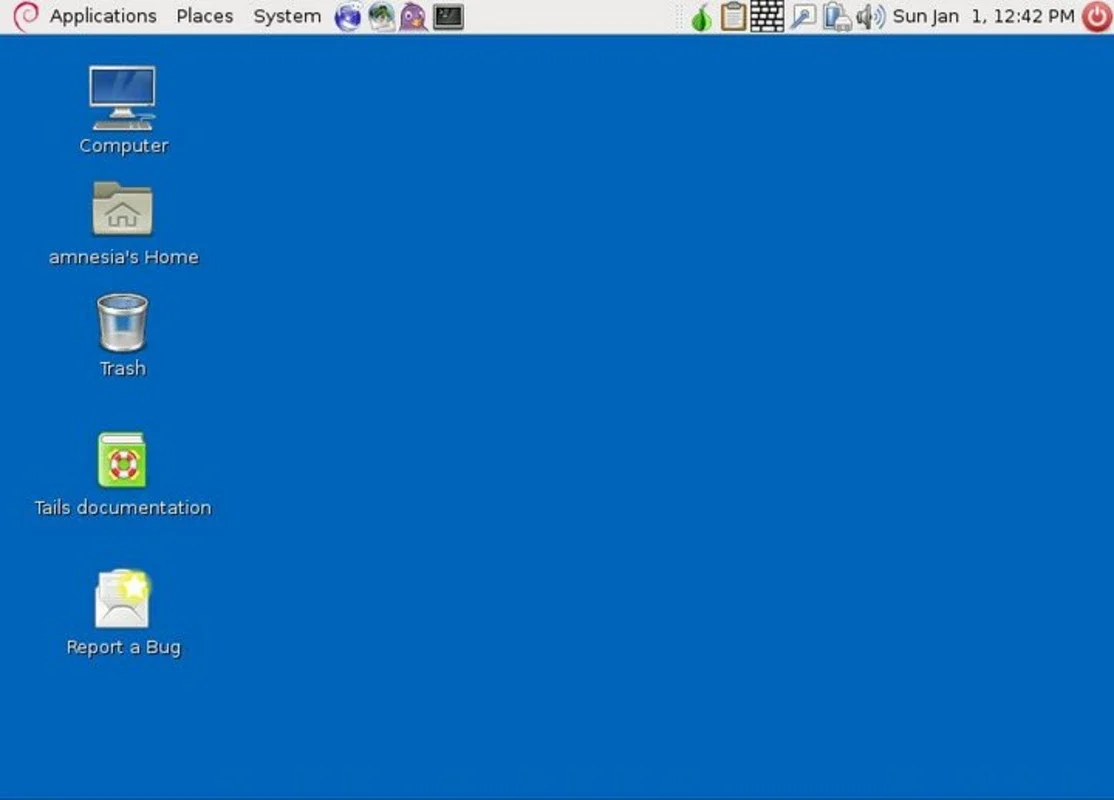
- Start Using Tails: Once Tails has loaded, you'll be presented with the GNOME desktop environment. You can now access the internet anonymously through the pre-configured Tor browser.
- Shut Down Securely: When you're finished using Tails, shut down the system properly to ensure that all data is securely erased from RAM.
Comparing Tails to Other Privacy Tools
Tails offers a unique approach to online privacy compared to other tools like VPNs or privacy browsers. While VPNs encrypt your internet traffic, they still rely on a central server, which can be a point of vulnerability. Privacy browsers, while enhancing security, don't offer the same level of anonymity as Tails, which completely isolates your browsing session from the host operating system.
Tails provides a more comprehensive and robust solution for users who require the highest level of online privacy and anonymity. It's particularly useful for journalists, activists, and anyone concerned about government surveillance or online tracking.
Advanced Features and Customization
While Tails is designed for ease of use, it also offers advanced features for experienced users:
- Command-Line Interface: For those comfortable with the command line, Tails provides access to a powerful terminal for advanced tasks.
- Persistence: While generally discouraged for security reasons, Tails allows for limited persistent storage for specific files and configurations.
- Customizing Applications: While the default applications are carefully selected for privacy, users can install additional applications, provided they are compatible with Tails' security model.
Limitations and Considerations
- Performance: Running Tails from a USB drive can be slower than running a traditional operating system from a hard drive.
- Resource Intensive: Tails requires a reasonable amount of system resources to run effectively. Older or less powerful computers may struggle.
- Learning Curve: While the interface is user-friendly, understanding the security implications and best practices for using Tails requires some learning.
Conclusion
Tails is a powerful and effective tool for protecting your online privacy and anonymity. Its unique design, combined with its reliance on the Tor network and its secure default settings, makes it an ideal choice for users who prioritize security and confidentiality. While it has some limitations, its benefits far outweigh the drawbacks for those who need a robust and secure way to access the internet.
Remember to always download Tails from the official website to ensure you're getting a legitimate and secure copy. Stay informed about security updates and best practices to maintain the highest level of protection.