Predator App Introduction
In today's interconnected world, securing your personal computer is paramount. Leaving your PC unattended, even for a short period, exposes it to potential threats. While numerous software solutions offer varying levels of protection, Predator stands out as a unique and effective approach to securing your Windows system. This innovative program transforms a standard USB drive into a sophisticated, physical security key, providing an extra layer of protection against unauthorized access.
How Predator Works: Simple, Yet Powerful
Predator's core functionality revolves around its ingenious use of a USB drive as a master key. The process is remarkably straightforward:
- Installation and Configuration: After installing Predator on your Windows PC, you simply insert your chosen USB drive. The software will then encrypt your system's access, linking it to the presence of that specific USB drive.
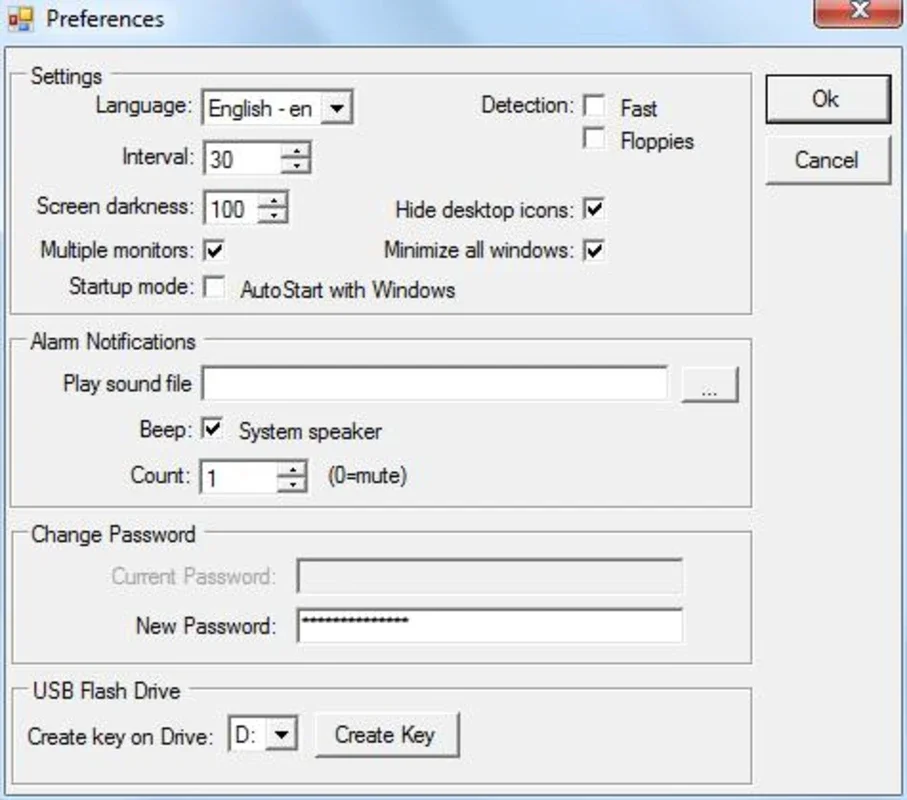
- Locking Your PC: Once the USB drive is securely connected, you can configure various security settings within Predator's intuitive interface. These settings allow you to customize the level of protection to your specific needs. Then, simply remove the USB drive. Within seconds, your PC will automatically lock, rendering it inaccessible to anyone without the key.
- Unlocking Your PC: To regain access to your system, simply reinsert the USB drive. Predator will instantly recognize the key and unlock your PC, returning it to its operational state.
Advanced Security Features: Beyond Basic Locking
Predator offers a range of advanced features designed to enhance your PC's security:
- Customizable Settings: Predator allows you to fine-tune its behavior to match your preferences. You can adjust the frequency of security checks, determine which desktop elements to hide while the system is locked, and even select custom notification sounds for added security awareness.
- Password Protection: As an additional security measure, Predator allows you to set a password to unlock the system, even if the USB drive is present. This is a crucial safeguard in case your USB drive is lost or stolen.
- Enhanced Security Protocols: Predator employs robust encryption algorithms to ensure your data remains secure, even if someone attempts to bypass the USB key restriction. The software regularly updates its security protocols to stay ahead of potential threats.
- System Integrity Monitoring: Beyond simple locking, Predator can monitor your system for unauthorized changes or intrusions. It can alert you to suspicious activity, helping you maintain the integrity of your system.
Comparing Predator to Other Security Solutions
Predator offers a unique approach to PC security compared to traditional methods. Unlike password managers or antivirus software, Predator provides a physical layer of security. This makes it particularly effective against physical theft or unauthorized access. While other solutions focus on software-based protection, Predator adds a tangible element, making it more difficult for unauthorized individuals to gain access.
Consider the following comparison:
| Feature | Predator | Traditional Security Software (e.g., Antivirus, Password Managers) |
|---|---|---|
| Security Type | Physical + Software | Primarily Software |
| Access Control | USB Drive + Optional Password | Passwords, Biometrics, Multi-Factor Authentication |
| Ease of Use | Simple and Intuitive | Can be complex, requiring technical knowledge |
| Additional Features | Customizable Settings, Password Protection | Malware detection, password generation, data encryption |
Predator: A Comprehensive Security Solution
Predator is more than just a simple PC locker; it's a comprehensive security solution that combines the convenience of software with the robustness of a physical security key. Its ease of use, coupled with its advanced features, makes it an ideal choice for individuals seeking a reliable and effective way to protect their Windows PC from unauthorized access. The ability to customize settings and add a password further enhances its security capabilities, making it a versatile tool adaptable to various security needs.
Conclusion: Taking Control of Your PC's Security
In a world where data breaches and cyber threats are increasingly prevalent, securing your personal computer is no longer a luxury but a necessity. Predator offers a unique and effective approach to bolstering your PC's security, providing an extra layer of protection beyond traditional software-based solutions. By transforming a simple USB drive into a powerful security key, Predator empowers you to take control of your PC's security and safeguard your valuable data.
This innovative approach to security makes Predator a valuable asset for anyone seeking to enhance their PC's protection. Its ease of use, coupled with its robust security features, makes it an excellent choice for both novice and experienced computer users alike.