Farbar Recovery Scan Tool App Introduction
Farbar Recovery Scan Tool (FRST) is a powerful, free utility designed to help users identify potential malware and security issues on their Windows computers. Unlike traditional antivirus software, FRST doesn't actively scan for and remove malware in real-time. Instead, it provides a comprehensive log file detailing various system processes, services, drivers, and registry entries, allowing users to manually analyze and identify suspicious items. This detailed approach makes it an invaluable tool for advanced users and security professionals, particularly when dealing with stubborn or undetected malware.
Understanding FRST's Functionality
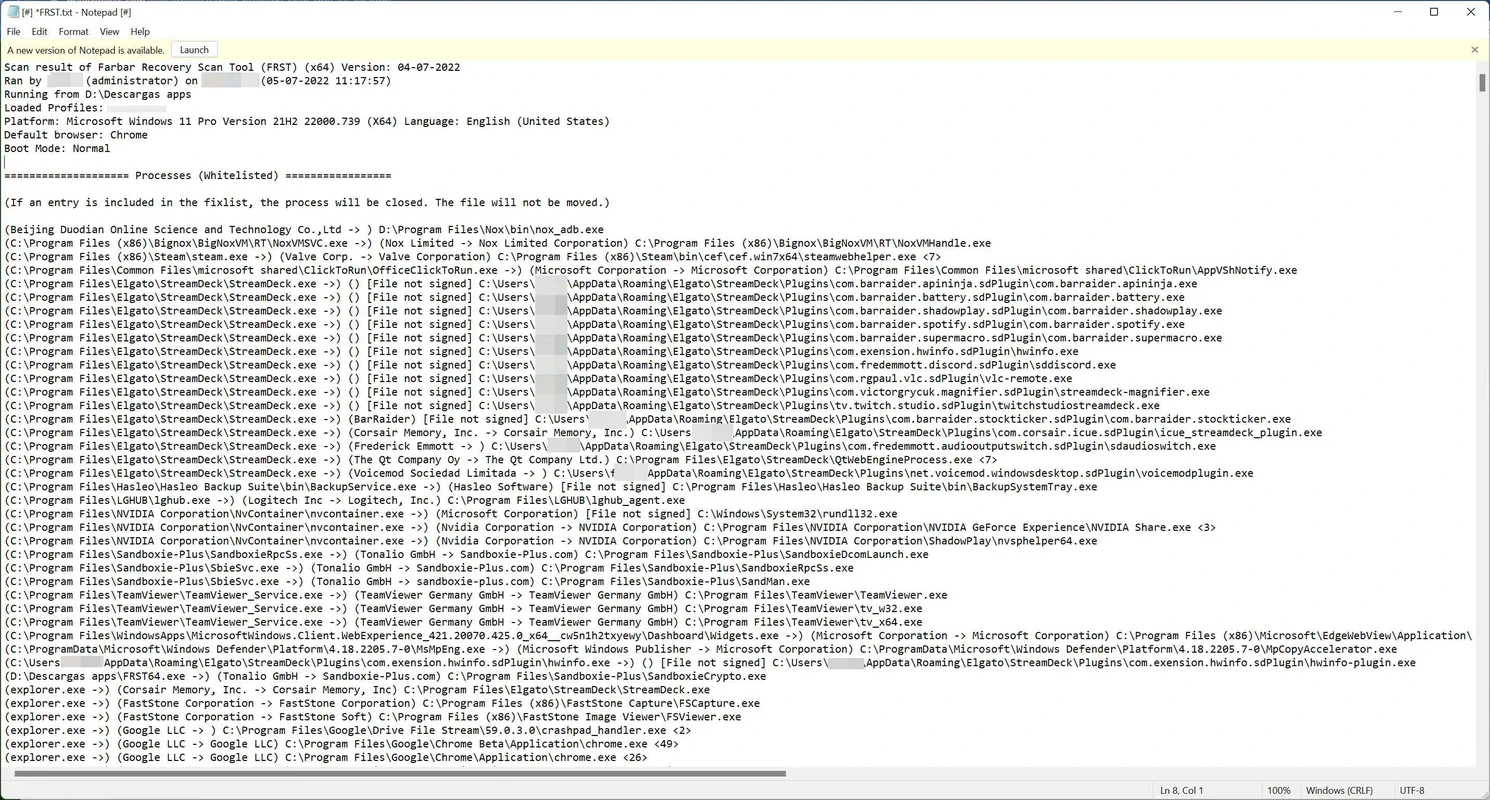
FRST operates by meticulously scanning various aspects of the Windows operating system, generating two text files: FRST.txt and Addition.txt. The FRST.txt file is the primary output, containing a wealth of information categorized for easy analysis. Let's explore the key sections:
- Active Processes: This section lists all currently running processes, including their paths and whether they are digitally signed. Unsigned processes are often a red flag, as legitimate software is typically digitally signed by its developer. FRST highlights these unsigned processes, making them easier to identify for further investigation.
- Registry Entries: FRST examines key registry locations, highlighting entries that might indicate malicious activity. This includes entries related to startup programs, services, and other system settings.
- Scheduled Tasks: This section lists all scheduled tasks, revealing any potentially malicious programs or scripts that might run automatically in the background without the user's knowledge.
- Internet Access: FRST identifies programs that have recently accessed the internet, a common indicator of malicious activity. This section helps pinpoint programs that might be communicating with command-and-control servers or sending sensitive data without authorization.
- Services: The services section lists all running Windows services, indicating their status, description, and whether they are signed. Suspicious or unknown services warrant further investigation.
- Drivers: FRST examines loaded drivers, highlighting those that are not digitally signed. Malicious drivers can often compromise system security and stability.
- Recent File Activity: This section lists files that have been recently executed or accessed, providing valuable insights into recent program activity. This can help identify potentially malicious files that have been recently run.
The Addition.txt file supplements the FRST.txt file with additional information, often including details about startup programs and other system configurations. Together, these two files provide a comprehensive snapshot of the system's state.
How to Use Farbar Recovery Scan Tool
Using FRST is straightforward. Download the tool from a reputable source, ensure you're running it from a trusted location, and run it with administrative privileges. The scan process is relatively quick, and the resulting text files are generated in the same directory as the executable. The key is to carefully review the generated logs, looking for any suspicious entries or patterns. This requires a good understanding of Windows system processes and configurations. If you're unsure about an entry, it's best to consult online resources or seek assistance from a security expert.
Interpreting FRST Results
Analyzing the FRST output requires careful attention to detail. Look for:
- Unsigned Processes and Drivers: These are often a strong indicator of malware.
- Suspicious Registry Entries: Entries that point to unknown or unusual locations should be investigated.
- Unusual Scheduled Tasks: Tasks that run automatically without your knowledge or that execute from unexpected locations should be examined.
- Programs with Recent Internet Access: Programs communicating with unknown or suspicious IP addresses are potential threats.
- Recently Executed Files: Files that were recently executed from unusual locations or that have suspicious names should be investigated.
Remember, FRST only identifies potential problems; it doesn't automatically fix them. If you identify suspicious entries, you'll need to take further action, such as removing the malicious files or disabling the suspicious services. Always back up your system before making any significant changes.
Comparing FRST to Other Malware Detection Tools
FRST differs significantly from traditional antivirus software. Antivirus programs actively scan for and remove malware in real-time, while FRST provides a detailed log file for manual analysis. This makes FRST a valuable supplementary tool, especially when dealing with malware that has evaded detection by traditional antivirus software. It's not a replacement for a good antivirus solution but a powerful addition to a comprehensive security strategy.
Consider the following comparisons:
- Antivirus Software (e.g., Malwarebytes, Norton): These programs offer real-time protection, actively scanning for and removing malware. They are essential for proactive security, but they might miss some deeply entrenched or sophisticated malware.
- Rootkit Detectors: These tools specialize in detecting rootkits, which are types of malware designed to hide their presence. While FRST doesn't specifically target rootkits, the detailed system information it provides can sometimes reveal their presence.
- System Monitoring Tools: These tools monitor system activity for suspicious behavior. FRST complements these tools by providing a detailed snapshot of the system's state at a specific point in time.
Conclusion
Farbar Recovery Scan Tool is a valuable asset in any security professional's or advanced user's toolkit. Its detailed system analysis capabilities make it an excellent tool for identifying potential malware and security issues that might be missed by traditional antivirus software. While it requires manual analysis and a good understanding of Windows system configurations, the information it provides is invaluable for resolving complex malware infections. Remember to use it responsibly and always back up your system before making any significant changes based on its findings. It's a powerful tool, but it's not a magic bullet; it requires careful interpretation and informed action.