Snort App Introduction
Introduction to Snort
Snort is a highly regarded open - source tool in the realm of network security. It is designed specifically for network administrators, providing them with a means to closely monitor and analyze the traffic flowing through an IP network in real - time. This real - time analysis is crucial as it enables the detection of potential intruders and the logging of incoming packets, which is essential for maintaining the security and integrity of the network.
How Snort Operates
Snort functions by delving deep into network protocols. It is on the lookout for any abnormal behavior that could be associated with various types of probes and attacks. For instance, it can detect buffer overflows, which occur when a program tries to store more data in a buffer than it was designed to hold. Port scanning, another activity that Snort can identify, is often a precursor to more malicious actions as it involves an attacker attempting to find open ports on a network. Additionally, Snort is capable of detecting CGI attacks, SMB issues, and OS fingerprinting tests. By analyzing these aspects, Snort can effectively flag any unusual or potentially harmful activities.
The Flexibility of Snort's Rule - Based Language
One of the most notable features of Snort is its rule - based language. This language offers a great deal of flexibility, allowing network administrators to define precisely what data should be captured and what can be allowed to pass through the network. The scanning engine of Snort is modular in nature. This modularity is a significant advantage as it means that the functionality of Snort can be enhanced through the use of plugins. These plugins can be added to extend the capabilities of Snort, making it adaptable to different network security requirements.
Alerts and System Administration
When Snort detects suspicious network behavior, it sends out various real - time alerts to the system administrator. These alerts are vital as they inform the administrator of potential threats, allowing them to take immediate action. However, it is important to note that Snort is a command - line tool. This means that it requires a certain level of technical proficiency to operate effectively. Administrators need to be familiar with command - line interfaces to make the most of Snort's features.
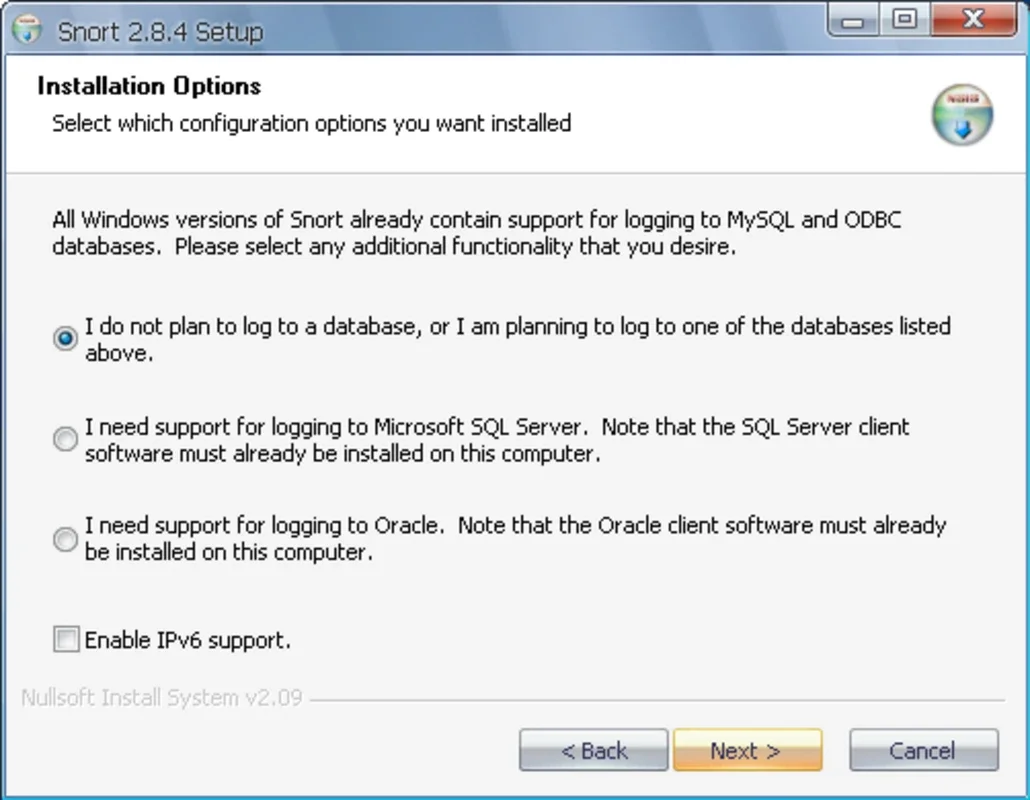
Compatibility and Configuration
Snort offers compatibility with important network - related technologies. It supports IPv6, which is becoming increasingly important as the Internet continues to evolve. In addition, Snort can be integrated with various database management systems such as MySQL, ODBC, Microsoft SQL Server, and Oracle. To get Snort up and running with the correct settings, administrators need to manually edit the snort.conf file. This file contains the necessary file and classification rules that determine how Snort will operate within the network environment.
Conclusion
In conclusion, Snort is an invaluable tool for network administrators. Its ability to analyze network protocols in real - time, detect intruders, and send out alerts makes it a key component in network security. Despite being a command - line tool, its flexibility in terms of its rule - based language and modular scanning engine, along with its compatibility with important technologies, make it a popular choice for those responsible for network security.